Subscription Tables Best Practices
 By Amy Oldham
By Amy Oldham
Protector can inform you and other designated users about case actions, event rule violations, or score-based incidents. Protector provides icons and messages in the portal that provide visual cues for many of these items. Additionally, the system’s subscription functionality lets you define whether Protector generates and delivers notifications for these items.
How Do Subscriptions Work?
A subscription is simply an automated notification. Your system’s configuration and event rules determine how Protector processes and generates these notifications. Protector delivers subscriptions via email, text, and/or SNMP trap to one or more recipients after an action triggers it. You dictate the recipients, the message (contents, formatting, attachments, subject line), conditions that must be met, and delivery method. Protector includes built-in templates for all subscription types. These readymade “shells” define the structure, format, and parameters for each subscription. When you launch the subscription wizard to create a subscription, Protector provides the default template for each subscription activity. You may use it as is or edit it to make a custom template for any subscription.
As mentioned, the subscription templates contain all required parameters, which include field placeholders, table placeholders, headings, and other transitional text. When Protector generates a subscription, it populates all placeholders with the applicable values for whatever activity triggered it.
Where Are Subscriptions Set Up?
If you have appropriate security permissions, you can add, edit, and maintain subscriptions in your Protector portal. To do so, click the ‘Settings’ icon in the top right and then select its ‘Setup’ option. Protector opens the Subscriptions grid shown here by default.
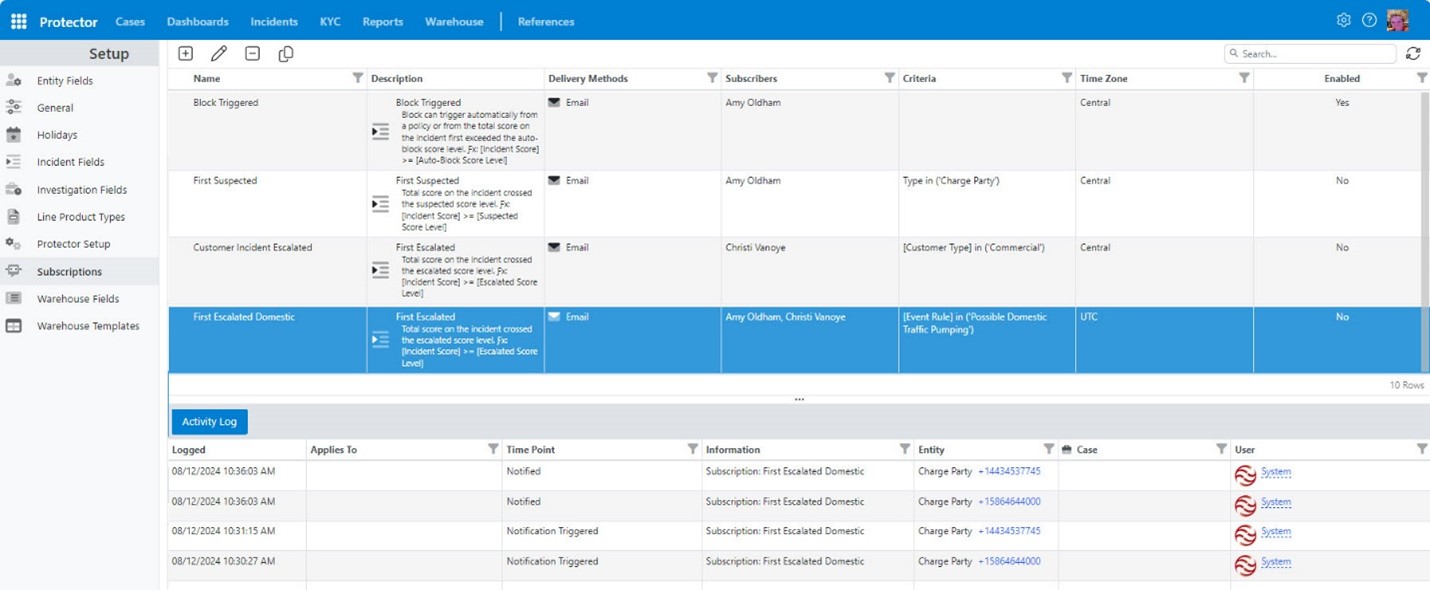
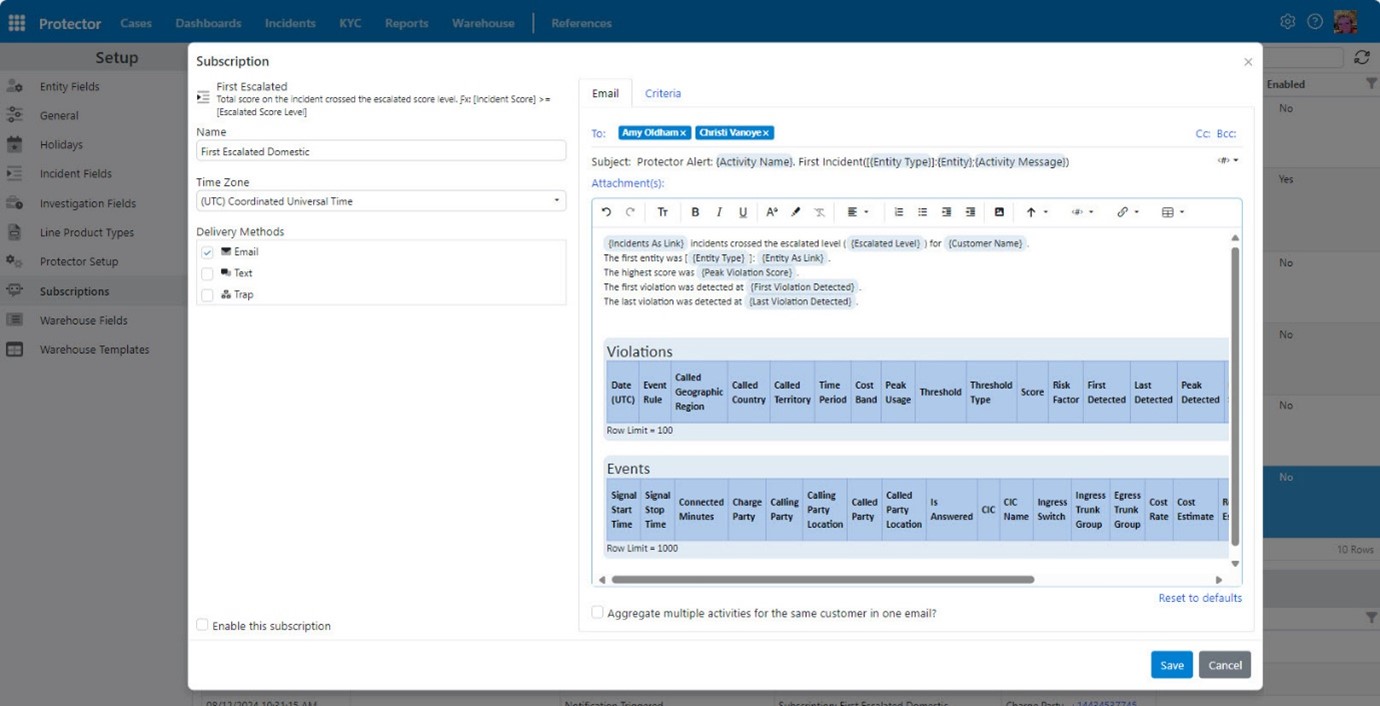
For this example, let’s look at the ‘First Escalated Domestic’ subscription. You can see it includes tables.
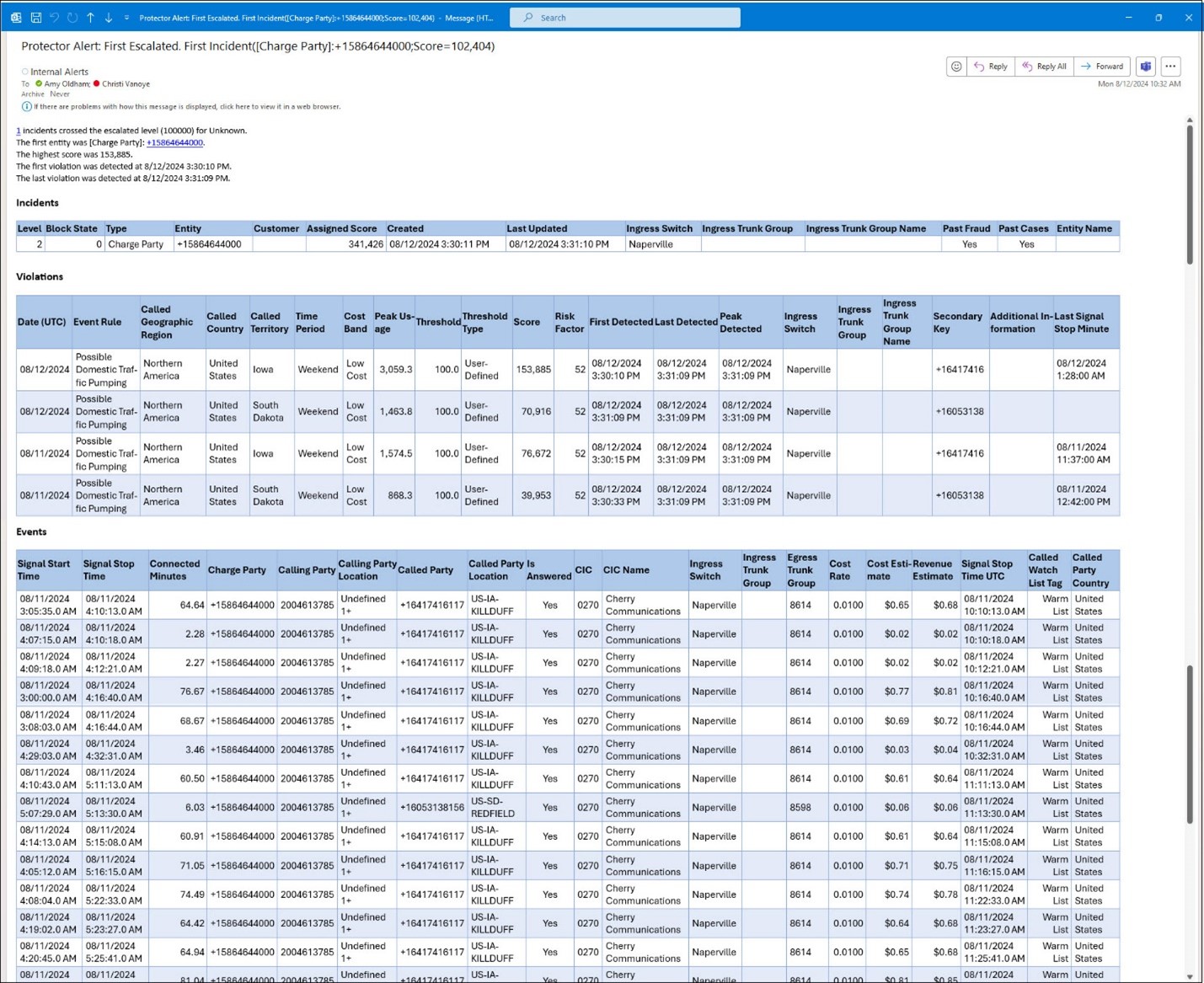
And the email Protector generates from this subscription looks like this example. Notice the Events table embedded at the end of the email body.
Why Does Table Use Matter?
Protector makes the Events, Incidents, and Violations tables available for use in subscriptions. You may use them in in two ways—embedded in the body of the subscription email or attached to it. The tables contain and present different data, so it’s important to describe each one.
- Incidents: this term describes an occurrence of event rule violations grouped by entity. Inserting this table provides details for the entity whose activity triggered the subscription. Including it in a subscription does not affect its delivery time. It’s the top of the hierarchy and has few rows.
- Violations: an incident may have multiple violations. Inserting this table in a subscription typically provides the best information for researching the rules and scores that triggered the subscription notification and does not impact delivery time.
- Events: events are the individual records that comprise a single violation. The most common reason to include this table in a subscription is to speed research. Attaching/embedding the table in the subscription lets you view event (call record) data directly in the email’s body or attachment without logging into the portal, which is especially useful on nights and weekends. However, it is NOT best practice to insert the Events table in your subscriptions without understanding the power of this feature. Protector’s workflows determine the order it completes tasks. Because Protector must wait to build the warehouse before it can attach or embed it in a subscription, it can take slightly longer (up to 1-3 minutes when the warehouse has millions of rows or system resources are diverted to another task such as reporting) to deliver versus a subscription that does not include the Events table. You don’t need to remove the Events table from all subscriptions; instead, it’s important to understand its impact.
What Action Do I Need to Take?
This article provides best practice recommendations related to Protector’s subscriptions and their ability to include tables. This information is not urgent nor meant to be alarming. Instead, this educational article allows you to make an informed decision about including tables in your subscriptions by default. Before inserting the Events table in a subscription, consider:
- The subscription activity. Because blocking occurs in very high score situations where every second counts, it’s important to get a ‘Block Triggered’ notification as soon as possible. As a result, Equinox recommends you not include the Events table in ‘Block Triggered’ subscriptions.
- What happens behind the scenes. Although Protector can instantaneously generate an incident and notify you about it, it cannot instantly compile the warehouse. So, even if a subscription does not contain the Events table, Protector must compile every event record for the rule and score violations the comprise the incident. Typically, Protector completes this process in the time it takes you to log in to the portal and locate the incident. Therefore, most users don’t experience or notice any appreciable delay in receiving subscriptions with the Events table.
- Performing a test to address concerns. If you have an existing subscription (for example ‘First Escalated’) that contains the Events table, make a copy of it. Remove the Events table from the copied subscription and rename the revised copy as ‘First Escalated No Events’, for example. Note when the subscription with the Events table arrives versus the one without it.
- Volume being monitored. Systems that have tens of millions of warehouse rows are more likely to experience the slight Events table subscription lag than systems with lower volumes.
- System resources. Systems that run at or below the recommended hardware specifications are more likely to experience the Events table subscription lag because Protector must prioritize its workflow processing.
Where Can I Learn More?
Our mission is to help telecom companies and service providers protect and optimize revenue. Helping you succeed in those areas is vital to our very existence. So, we’re more than solutions suppliers; we are your partner. Our training, implementation, and support teams provide one-on-one, personalized assistance to maximize the benefit from every tool and feature we offer. If KYC is a new concept or you’d like to explore best practice recommendations, we can help.
- Christi Vanoye has extensive FMS (fraud management solution) experience due to training every Protector implementation since 1998. Based on those interactions, she helps ensure Protector is fully and appropriately configured for each organization’s specific market and business line. During initial system training, she can help your team set up subscriptions that support your company’s specific business needs. Schedule online training with Christi to set up, review, or edit subscriptions in your system, by contacting Training@Equinoxis.com.
- Equinox Support is comprised of knowledgeable, friendly folks who are happy to help. Email Support@Equinoxis.com with questions about Protector’s subscriptions. To reach them by phone, call (615) 612-1225 Monday–Friday from 7:30 to 4:00 (Central).



